Secure AI Development with Commands: Beyond Static Rules
Turning security checklists and best practices into executable, self-updating workflows developers actually use.
AI coding assistants are transforming how developers work - and how organizations must think about security, compliance, and governance.
By now, most developers are familiar with Cursor Rules - a simple yet powerful way to define safe defaults for AI behavior inside the IDE.
But Cursor Commands, a newer capability, are still unfamiliar to many teams. They take things much further - turning your AI from a passive assistant into an active, policy-driven teammate.
Claude offers a similar capability called Claude Skills, which enable structured workflows that run transparently inside the LLM - rather than as direct /commands in an IDE. In this post, we’ll focus on Cursor, which brings that concept into the developer environment through explicit, runnable commands.
In this post, I’ll share how we built a list of practical security commands for Cursor (available here on GitHub), and how you can adapt them to your own stack.
Understanding cursor rules
Cursor rules has become quite popular - and for good reason. It lets teams define a system prompt that gives the AI clear, persistent guardrails and safe defaults inside the IDE.
Beyond enabling teams to tailor security rules to their own preferences and workflows, the real power lies in the community’s ability to establish shared standards. Great open examples - like matank001/cursor-security-rules - show how teams can contribute reusable templates that not only restrict sensitive actions but also encourage consistent, secure development practices across the ecosystem.
For example:
## 8. Avoid Hardcoded Secrets
Do not hardcode passwords, tokens, or secret keys in source code.
Use environment variables or a secure configuration service.In essence, cursor rules defines the AI’s secure baseline - ensuring it operates within defined boundaries and follows good engineering practices.
It can define both what the AI should and should not do, acting as a persistent policy layer that always applies in the background.
However, cursor rules is a static configuration. It always applies globally - not contextually.
It doesn’t allow targeted actions on specific files, commits, or functions with deep context.
That’s where Cursor Commands come in - enabling context-aware, on-demand workflows right inside your IDE.
Cursor Commands - From Static Rules to Smart Workflows
Cursor Commands live inside a .cursor/commands/ folder and let developers define reusable AI-powered workflows that can be triggered directly from the IDE using a slash command (/).
Each command is written in Markdown with a simple YAML header - like a script that tells the AI how to act in specific situations.
For example - Address Github PR Comments:
Process outstanding reviewer feedback, apply required fixes, and draft clear
responses for each GitHub pull-request comment.
## Steps
1. **Sync and audit comments**
- Pull the latest branch changes
- Open the PR conversation view and read every unresolved comment
2. **Plan resolutions**
- List the requested code edits for each thread
- Identify clarifications or additional context you must provide
3. **Implement fixes**
- Apply targeted updates addressing one comment thread at a time
- Run relevant tests or linters after impactful changes
4. **Draft responses**
- Summarize the action taken or reasoning provided for each comment
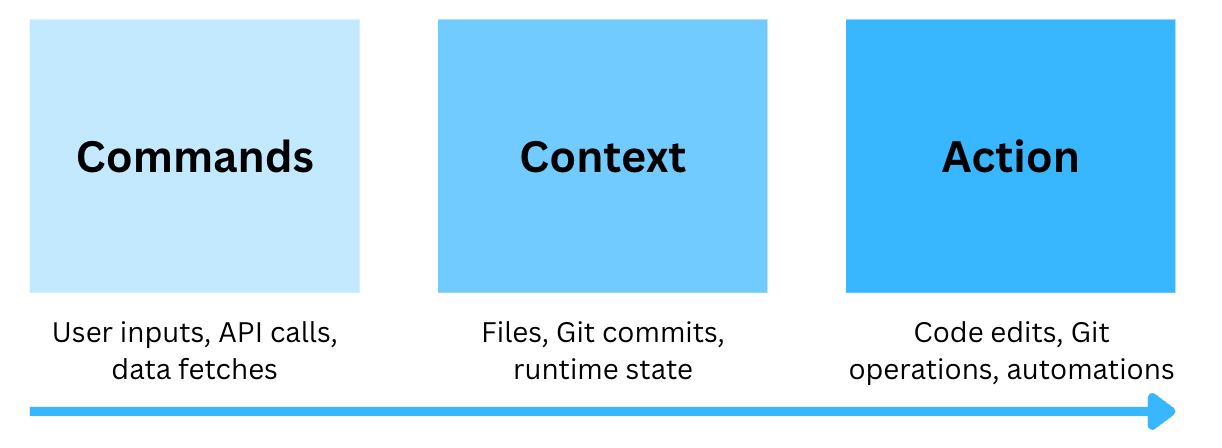
- Link to commits or lines when clarification helps reviewers verifyWhen a developer types a workflow command such as /address-pr-comments, Cursor automatically executes the corresponding workflow using real-time project context - like open files, Git diffs, and conversation threads.
Each command can run external tools, fetch live data, and apply context-aware reasoning to streamline developer tasks directly from the IDE.
This turns AI from a conversational helper into a repeatable, version-controlled automation engine for engineering tasks.
There are already great developer examples available publicly, such as:
👉 hamzafer/cursor-commands - a collection of reusable commands for reviews, refactoring, testing, and productivity.
👉 ComposioHQ/awesome-claude-skills - similar for Claude, showing structured Skills that can run automatically within the model’s reasoning flow.
Using Cursor Commands for Security and Compliance
At Pluto Security, we’ve been researching how this feature can go far beyond productivity - into secure development and compliance automation.
We treat .cursor/commands as a policy execution layer: a way to define repeatable, reviewable, and context-aware actions that developers can trigger at any time.
We designed commands for repeatable security tasks that developers can run directly in their workflow - each command can fetch live data from trusted internet sources (official docs, advisories, best-practice repositories) to stay always up-to-date.
The best part? You can plug in your own stack:
Compliance SaaS platforms (SOC 2, ISO 27001, HIPAA, CAIQ Lite)
Internal security documentation or wikis
CLI Tools (Snyk / Trivy / AWS..)
Scripts
Each command execution can automatically pull the most recent guidance (to ensure alignment with the latest policies, standards, and compliance frameworks) run your own custom CLI commands and execute pre-made python scripts in the right context.
This means developers use simple, reusable commands created by security teams - but those commands evolve in real time, keeping code and compliance aligned.
Examples
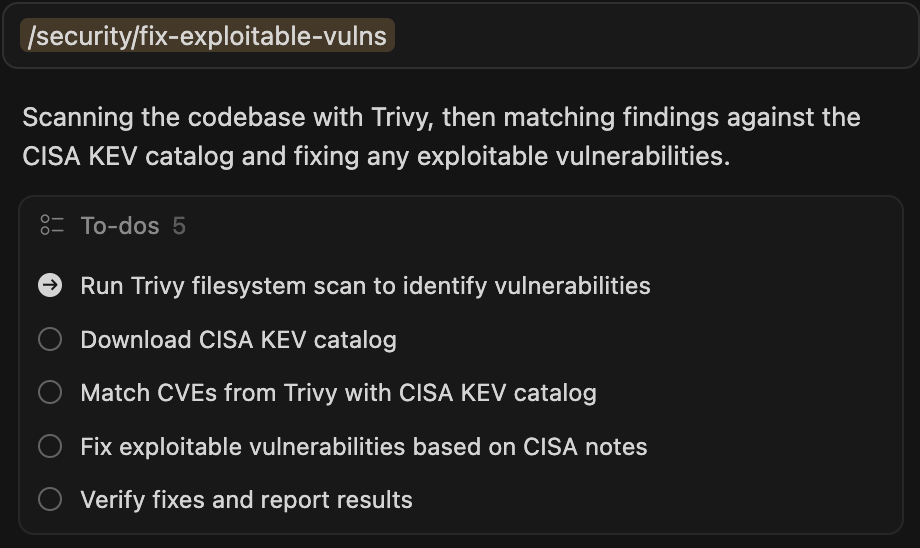
/fix-exploitable-vulns - Scans your codebase with Trivy (CLI), downloads the live CISA Known Exploited Vulnerabilities (KEV) catalog (Web Surf), matches discovered CVEs against actively exploited vulnerabilities, and attempts to create a fix based on remediation steps online
/validate-compliance - Fetches your company’s live compliance controls -SOC 2, ISO 27001, HIPAA, GDPR, etc. (Web Surf) from your compliance management API or configuration store, compares them against the current code context or repo configuration using automated scanning tools, and then fixes or flags misalignments, ensuring your code continuously meets policy requirements.
Bridging Policy and Practice
This model lets security teams expose security workflows as developer-friendly commands - consistent, current, and organization-aware - enabling developers to resolve issues during the development process. Developers gain frictionless security automation. Security teams gain continuous assurance.
It’s the bridge between policy and practice - security that moves at the speed of code. Our library of commands and integrations keeps growing - and we welcome your ideas to keep growing it.
Connecting your own stack
You connect your own stack by editing the command prompts (Python scripts, CLI, Links).
For example for other CLI:
Run a scan on S3 with AWS controls
# change it to reference your aws stack:
aws s3api get-bucket-policy-status --bucket data-bucketFor links resourced (For compliance for example), just embed the framework source in the prompt:
Scan against the SOC2 framework defined at
https://api.compliance-saas.io/frameworks/soc2orScan
using my local framework at ./frameworks/custom-soc2.json.One Repository, Two Layers of Control
To keep everything organized and transparent, both layers live in the same repository :
📦 repo/
└── .cursor/
├── rules/ # Guardrails & boundaries
└── commands/ # Secure workflows & policy logic.cursor/rulesDefine baseline policies allowing to create Guardrails & boundaries.cursor/commandsExecute secure workflows for Automation & accountability
To use this project, add it to the root directory of every project so its configurations take effect or add it to the local ~/.cursor/commands to apply to all. Review and update it periodically to ensure it stays aligned with the latest standards.
Secure Commands GitHub
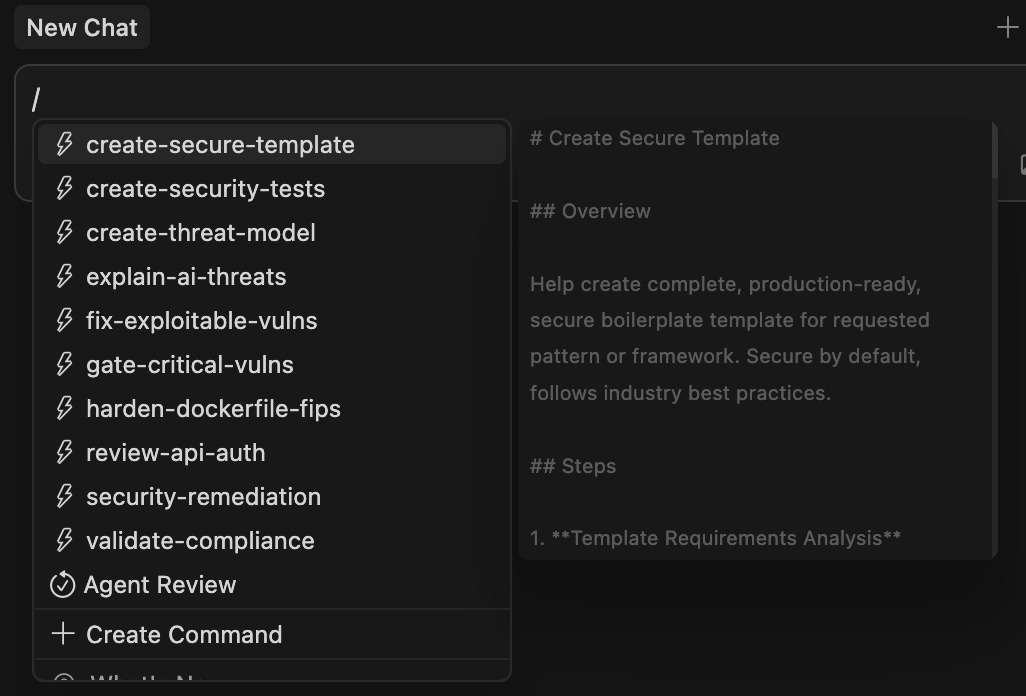
Based on our research, We’ve built the first public GitHub with secure DevOps commands - covering threat modeling, vulnerability fixing, configuration hardening and much more.
To keep using generic developer commands, we recommend splitting the commands into dev, security folders.
We’re continuously expanding it with real-world examples, If you have more security or compliance use cases - let us know!
Final notes
Cursor rules are a solid foundation - but they’re just the start.
Real security and compliance in AI development don’t come from static guardrails; they come from codified, enforceable behavior.
If you’re bringing AI-powered tools into your SDLC, treat them as part of your security perimeter - because they are.
At Pluto, we’re enabling enterprises to use AI Builders securely.
Want to learn more? Let’s talk.